 For quite some time, my computer at work has exhibited many signs of a malware infection, but none was ever to be found.
For quite some time, my computer at work has exhibited many signs of a malware infection, but none was ever to be found.
More specifically, at random times (usually when quickly typing a URL into a web browser) I would end up on the wrong page - usually a page trying to convince me that I'm wanted by the FBI, or trying to sell black market Viagra ('scuze me, "V1@gkr4"), or other kinds of annoying spam.
Of course, when you see something like this, you immediately assume you are infected by a virus or have some kind of malware. And I did all the right things - boot from a known-good recovery disk and run all kinds of scanners. And none of them revealed anything.
So what was going on here? The answer is that I got hit by a perfect storm of coincidence.
To understand the answer, you must understand that my job has gone through many acquisitions over the years. I've been working with the same team of coworkers for five different companies as our group has been acquired and divested over the past 20+ years. When acquisitions happen, they generally do not involve an immediate replacement of computer equipment, and my main computer, being less than three years old, has not been replaced since the most recent acquisition.
And here's what happened. As is typical for any computer installed on a corporate network, the computer is configured to append the company's DNS domain suffix to any non-qualified host-name. For example, if my computer is configured for a DNS suffix of "myemployer.com", then an unqualified URL like "http://foo" will automatically resolve to "http://foo.myemployer.com".
Normally, this is a good thing, since you don't need to remember to type in the full domain name. It is especially important if your employer's domain name is very large (e.g. sitename.statename.region.myemployer.com)
But what happens when that domain ceases to exist?
That's what happened to me. After the last acquisition, the new company decided it didn't want to continue paying the registration fees for the old company's domain, so it let the registration expire. And the domain was quickly bought up by someone who is hosting scamvertising. So now, every DNS request for the old domain gets redirected to the scam site.
At this point you can probably figure out what was going on.
I frequently type partial URLs into my web browser and let its autocomplete function fill in the rest of the URL based on my bookmark list or my browsing history. But sometimes the computer is a bit slow or my typing is a bit fast and I press the ENTER key before the browser gets a chance to auto-complete the URL. So the system takes whatever I had typed so far, appends the old company's domain suffix to it and tries to fetch that page - which always goes to the scamvertising site.
Of course, I didn't figure this out for over a year.
A few weeks ago, I decided once and for all to figure out what was going on. I already knew that the former employer's domain had been taken by scammers. I figured out that URLs without domain names would go there, but I hadn't managed to put two and two together and was instead considering many other incorrect possibilities.
Could it be malware? It would be very strange malware that only redirects URLs without domain names. It happened whether on the company's network, on my home network, or when connected to a VPN. Other company computers exhibited the same problem, but non-company computers didn't. Could it be some weird side effect of the company's security software? Looking at debug traces from my web browsers indicated that I was not receiving any HTTP redirect pages. And all of my web browsers exhibited the same symptoms.
In desperation, I decided that the best approach would be to run a packet sniffer program (the wonderful Wireshark) on my computer to see what the network traffic really is. So I started capturing packets, typed in a bogus URL into the web browser, saw a scamvertisement page, and went to look at the traffic. And there I saw it - the DNS request going out to the Internet had the old employer's domain name suffixed!
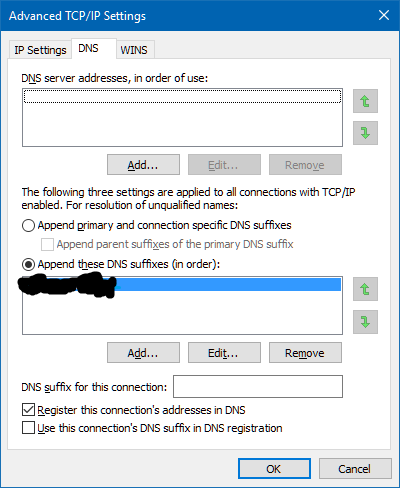
At which point, I finally figured it out. I went into Windows' configuration and removed the old employer's domain name from the DNS suffix list and the problem immediately stopped. With that one simple change, requests for bogus URLs now return error pages, as they are supposed to.
And so, as a service to you, my reader, here is how to fix this particular problem on your Windows system:
- Open the Windows control panel. On Windows 10, go to the start menu and look in the "Windows System" folder for it.
- Click on the "Network and Internet" category
- Click on the "Network and Sharing Center" category
- Click on "Change adapter settings" from the left-side column
- Right-click on your network adapter (probably "Wi-Fi" or "Ethernet") and select "Properties" from the popup menu.
- In the list of configuration items, scroll down and select "Internet Protocol Version 4 (TCP/IPv4)" and click "Properties"
- Click the "Advanced" button
- Click on the "DNS" tab
- Select the DNS suffix you want to delete and click "Remove"
- Click "OK" on all the windows that have opened, in order to save the change
And that should be that. This procedure should be very similar (if not identical) on any version of Windows you are likely to be running.
If you are running Linux or macOS, the procedure is different. Not hard, but I will leave it as an exercise for the reader.

2 comments:
I can't remember, but I think those settings might be adaptor specific as well, If so then if you have a laptop with a network jack and a wireless adaptor you would have to do this for each of the adaptors as well.
I can't speak for all platforms, but on Windows 10, the DNS settings are shared by all network interfaces, so it was only necessary to change it in one place.
I was extra paranoid and checked all the other locations (IPv4 and IPv6 on every interface), but they all showed the same configuration.
Post a Comment